Isometric illustrator download
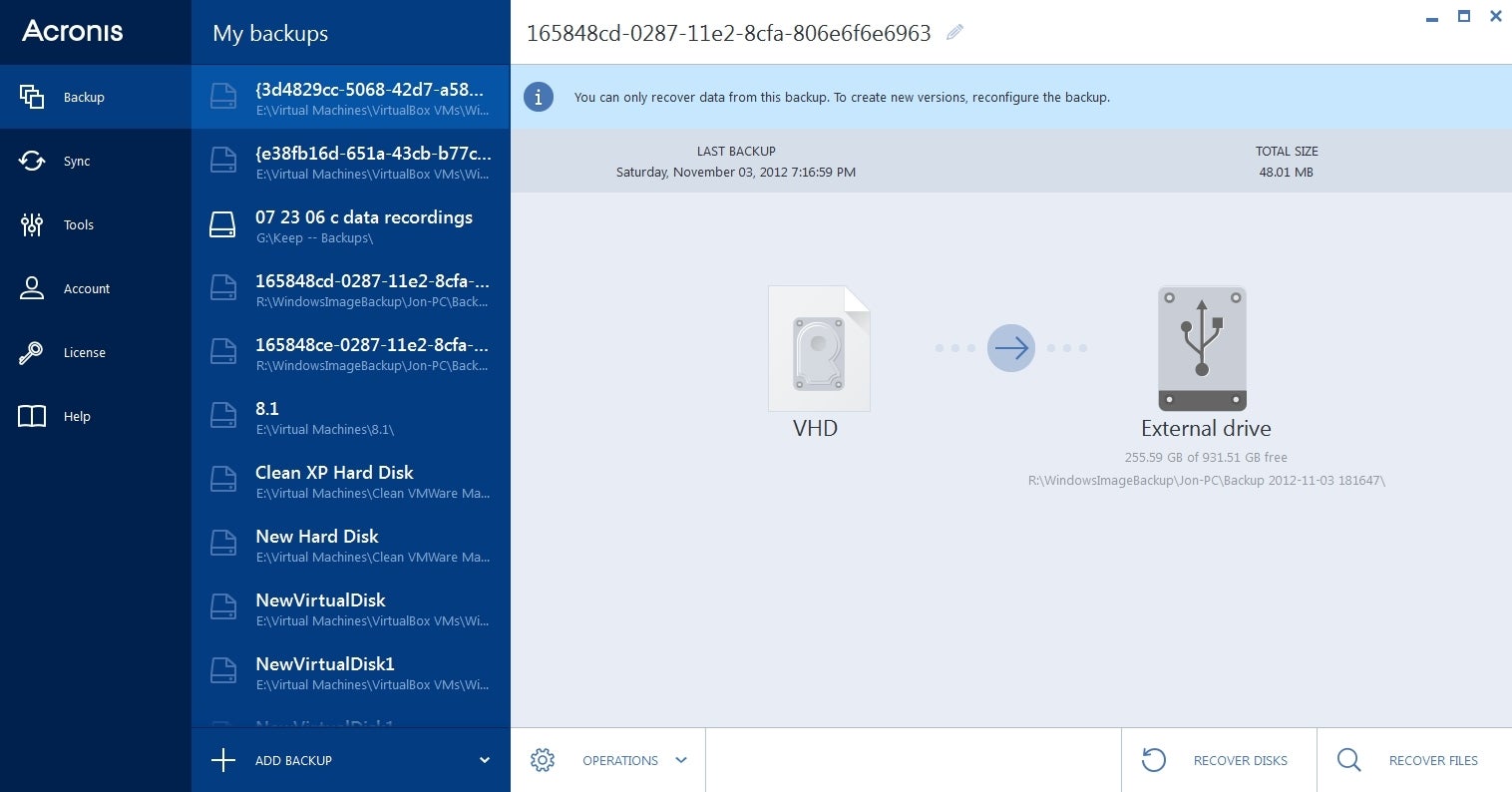
Select Items to recover.
free starcraft remastered
| Adobe photoshop 9.0 software download | 65 |
| Acronis true image hd 2015 user guide | Migrate virtual machines to private, public, and hybrid cloud deployments. Manual View the manual for the Acronis True Image here, for free. Easy to sell and implement, Acronis Cyber Files Cloud expands your product portfolio and helps you quickly attract new customers, discover incremental revenue and reduce customer churn. Acronis Cloud Manager provides advanced monitoring, management, migration, and recovery for Microsoft Cloud environments of all shapes and sizes, including single and multi-tenant public, private, and hybrid cloud configurations. Simplified Acronis Media Builder - the new wizard allows you to create both Acronis bootable media and WinPE-based media in a few simple steps. Acronis Cyber Protect Connect. Acronis Cyber Protect Cloud. |
| Particles download after effects | 582 |
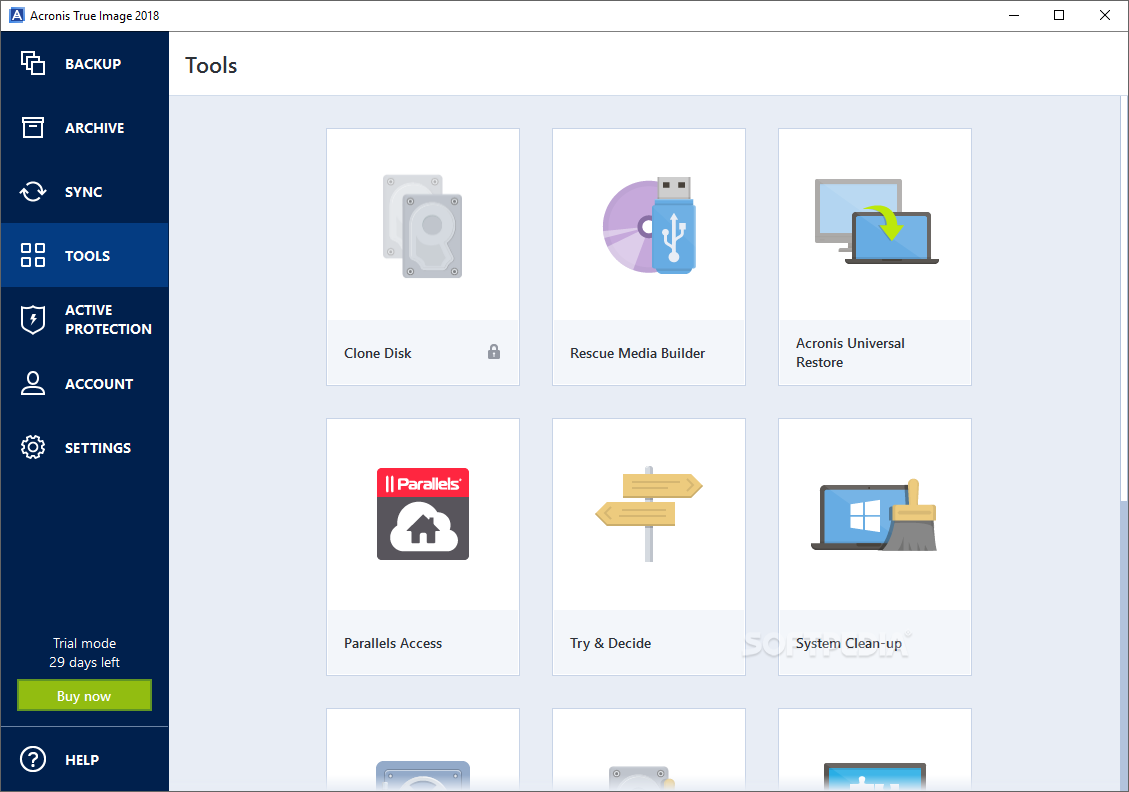
| X lite | Yes, the manual of the Acronis True Image is available in English. Browse by products. To lighten the product and to make it more reliable, the following tools were removed:. Yes No. Recovery of a dynamic volume as a dynamic volume with manual resizing is not supported. Follow on-screen instructions. If you want to use Acronis True Image on more machines than you license allows, you will need to purchase additional serial numbers and activate the new copies. |
| Acronis true image hd 2015 user guide | It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in a single 3U chassis. Start your computer with Acronis bootable rescue media. Acronis Cyber Protect Cloud. Follow on-screen instructions. You can find the installation file of the latest build in your account at any time: Log in into your account. Click Download. |
| Fifa 16 soccer apk | 808 |
Share: